Excellent! There’s certainly a lot to unpack, but being able to twist all these little knobs is part of the beauty of Linux.
StarkZarn
- 10 Posts
- 44 Comments
Hey, much appreciated!

 1·19 days ago
1·19 days agoThe primary thing is rather than “dumb” flood routing, you can choose the path your message takes to its destination; as a repeater operator you can also choose the path it takes to repeat out. Its a slight compensation to people carelessly placing infrastructure nodes with poor configurations in poor places. Not perfect, but better. Adoption is much, much lower though, and the licensing is not copyleft.

 2·19 days ago
2·19 days agoMeshcore does address some of the biggest shortfalls of Meshtastic, but I absolutely HATE that they’re positioned to either rugpull, or setup a perpetual “freemium” model. It’s also not interoperable, so if Meshcore is to work, it needs the numbers like Meshtastic has.

 3·19 days ago
3·19 days agoYeah, so far the most prevalent thing around my area has been “it’s a hobby for the sake of being a hobby.” No one does anything terribly useful or important with it. I can tell you that I would certainly never rely on it as a form of emergency communication.
Love me some graylog
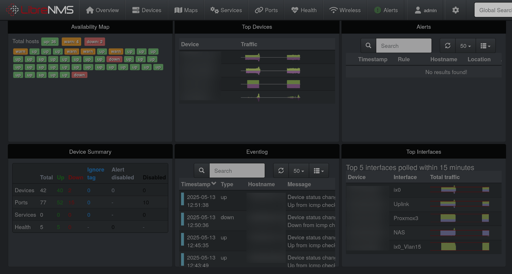
LibreNMS, which is a modern fork of observium.

 1·2 months ago
1·2 months agoYes! Qsl cards are very much still alive and well. Some traditions will never die. The special event stations are fun to get cards from.
Super cool anecdote on the telescope thing, I’ve never heard of that.
I hope you get back on the radio, it’s a great hobby. It’s a nice stress relief outlet for me these days too.

 2·2 months ago
2·2 months agoLove to hear things like that! When I first got licensed the solar cycle was utter trash. We’re past the peak now, but band conditions are still pretty good generally. A few watts and a wire will still get you somewhere with CW and some other forward error corrected modes (like FT8). I have a lot of fun with the digital stuff like AREDN, but it’s definitely a different ball game and the old school SSB-based radio still has its place in my heart.

 2·2 months ago
2·2 months agoFalse positive what? I didn’t give any specific examples of alerts, just simply monitoring metrics. Are you referring to the note on the Dnsmasq memory leak?

 6·2 months ago
6·2 months agoFor any hams here, maybe this blog post will be up your alley. 73!

 1·3 months ago
1·3 months agoThe OIDC settings in the Authelia config reference were the most nebulous to me, but they weren’t entirely stumping. The hard part was interpreting whether my errors stemmed from an issue on the client application side or on the Authelia side.
I would imagine you could likely extend the config snippets from my post to work in your situation with a few tweaks. The big lift, the OIDC provider is covered, so I’d be curious to hear what else you have to tweak!

 6·3 months ago
6·3 months agoHey good for you, that’s awesome! My home network is also dual stacked.
You’re right about the apples to oranges comparison, but it’s not so wildly off, because the commentary is on adoption of new standards, regardless of bolt-on “fixes.” Unauthenticated SNMP went through three revisions prior to adding authentication and encryption support.

 6·3 months ago
6·3 months agoAnd IPv6 was codified in RFCs and first addresses issued in 1999 but look where we are now. I’d bet your corporate network doesn’t use IPv6 still. It’s unfortunate, but sometimes the wheels of change are slow.

 5·3 months ago
5·3 months agoNagios is a premium offering. They have some open source components, but the software model is absolutely not built around the spirit of GPL.
Zabbix is the obvious alternative in my mind, and it is AGPLv3, so absolutely in the same spirit as the LibreNMS license. It’s a slightly different tool though, and less network-specific. Having used both, I prefer LibreNMS for specifically network monitoring, it’s laid out to cater more to an ISP-type entity running it, and I like that. Zabbix still gets my wholehearted stamp of approval though.

 5·3 months ago
5·3 months agoUpdated the post to reflect your feedback here. Thank you!

 7·3 months ago
7·3 months agoYou are absolutely correct, thank you. Sadly a bunch of devices still don’t support it, even in 2025 (like my microtik switch) for example. I will absolutely add a note about that though, thank you!

 3·3 months ago
3·3 months agoI absolutely have and used it for a while before landing on opensuse microos primarily. I absolutely see the benefit and enjoyed the git-centric nature, keeping flakes in repos with a flavor for each machine. What I didn’t enjoy, however, was the seemingly poor documentation. Quite frankly too, the drama surrounding the community doesn’t inspire confidence either. I decided I ought to try out guix but haven’t gotten to it yet. I do actually still have one nixos VM that hosts some services for me and is built entirely on the concept of the impermanence flake. That was pretty cool.

 2·3 months ago
2·3 months agoExcellent! Let me know if there are specific things you’d like to hear about.




That’s a super valid question, as it seems sometimes that some of these things are configured in a way that begs the question “why?” As far as contributing to documentation, that’s a moot point. This is already in the man pages, and that’s exactly what I referenced in writing this post, in addition to some empirical testing of course. As far as implementation goes, I think that probably lies at a per distribution level, where not one size fits all. Although I don’t know of it off the top of my head, I’m sure there’s a security centric distro out there that implements more of these sandboxing options by default.